IndoXploit - a peek inside.
Last week a new file appeared on one of my servers. It was in an upload folder and was called indoxploi.php. I decided to play around with it and see what it does. It’s quite a thorough set of website exploits, specializing in defacing Wordpress websites, but with capabilities of doing a lot more. If you find this file, delete it!
 ](/images/indoxploit01.png)
](/images/indoxploit01.png)It’s not too clear what the intruders were doing on the system but my guess is that they are setting up the server in order to sell it on to another user, either a criminal gang or to a government (is there a difference?). The WP config files were put at a location where they could be linked to directly and would give easy access to an intruder. The main indoxploi.php file was password protected and the password could be sold on to anyone who wanted total control over the server.
The group behind it are the IndoXploit Coders Team and publish a range of other exploits. They are based in Bangkalan, Indonesia and specialise in PHP hacks. I think this script is an example of their IndoXploit Shell
The sections
 ](/images/indoxploit00.png)
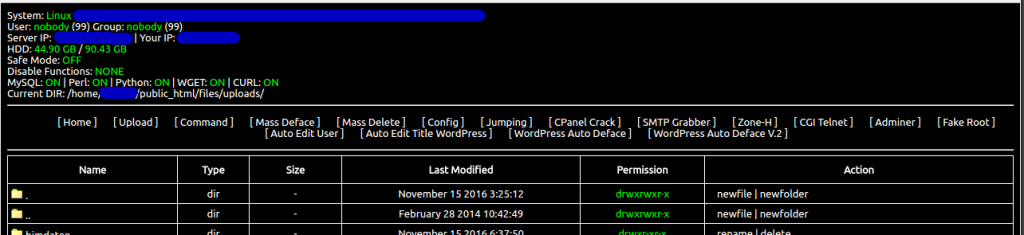
](/images/indoxploit00.png)Above is the page shown on startup. The directory listing is the listing from the account that has the script in. This script, on my server (CentOs 6) is running as nobody:nobody, so anything that it does is as that user.
[Upload] does what you expect, you can upload any file that you want on to the server.
[Command] is more interesting. The first thing the visitors did on my server was to run cat /etc/passwd this gives them a listing of all the accounts on my server. Note that it does not give them the passwords to the accounts. They can then run searches through those accounts to find anything that looks like a config file.
[Mass Deface] and [Mass Delete] are a couple of sections that I didn’t experiment with, but I guess that they do what you would expect.
[Config] will loop through all the accounts on the server, looking for configuration files and copying them into a folder as a file called username_Type.txt. The name of the folder is, on my server, idx_config and this is hardcoded into the script. It searches for a range of configuration files (Joomla, Drupal, Magenta etc, about 20 in total) and copying them with the Type set to the type of the config. It searches for the full path, not just the filename, so if you have installed in a non-standard location it will be missed.
[Jumping] will jump you to a different user account. You will see a list of the various accounts on the server, with clickable links to jump to them.
[CPanel Crack] will attempt to crack the cPanel password for the account.
[SMTP Grabber] tries to find SMTP login details but appears to be setup only for Joomla installations.
[Zone-H] I didn’t play with but it seems to deface the site and then automatically submit it to the Zone-H defacements archive.
[CGI-Telnet] didn’t work, but what it does is pull in a script stored on another server (pastebin.com for example) and run it. The script name is hardcoded but it shouldn’t be difficult to make it a user input.
[Adminer] will install adminer.php and run it for you. You will need to supply the login details, it’s not automatic, but presumably you will have them from running Config beforehand.
[Fake Root] hmm, not sure what this is supposed to do…
[Auto Edit User] allows you to add or modify a user name and password on a Joomla/Wordpress/etc CMS using the config files found by running the config stage.
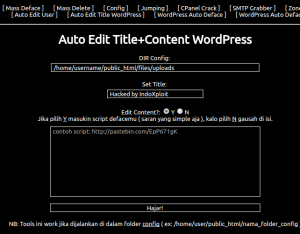
[Auto Edit Title/Content Wordpress], [Wordpress Auto Deface] and [Wordpress Auto Deface v2] do what they say I think, but I haven’t tested them.